热门话题
#
Bonk 生态迷因币展现强韧势头
#
有消息称 Pump.fun 计划 40 亿估值发币,引发市场猜测
#
Solana 新代币发射平台 Boop.Fun 风头正劲
这个扩展是假的,可能非常恶意 - 始终检查 _谁_ 发布了它(微软什么时候会对扩展的来源进行验证??)。如果你安装了这个扩展,请立即断开互联网连接,将该设备上的所有热钱包资产转移到安全的硬件钱包,并在 SEAL 911 向我们提交工单。



2025年8月9日
Is there a malicious solidity VSCode extension? It seems the version from `juan-blanco` has more downloads/better reviews, despite being new. The version from `juanblanco` has bad reviews, less downloads, but longer history. The newer version DID NOT WORK, so I looked further. 🧵


在这里进行了快速深入的研究

2025年8月9日
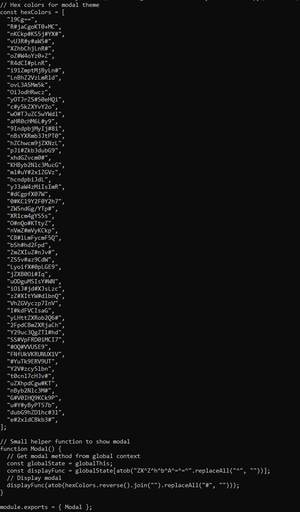
so the malicious part is in the `modal.js` file; TL;DR is the following. The obfuscation applied is:
- `hexColors` array holds Base64 fragments padded with `#`
- Reversed, joined, stripped of `#`, Base64-decoded
- Decoded code executed via hidden `eval` (`ZXZhbA==`)
The behaviour is:
- Targets Windows (`win32`) and macOS (`darwin`) only
- Disables `TLS` certificate verification (`NODE_TLS_REJECT_UNAUTHORIZED = "0"`).
- Fetches remote JS from:
Windows → p92nd[.]pages[.]dev/cj292ke.txt
macOS → p92nd[.]pages[.]dev/ufjm20r.txt
- Executes fetched code via `eval` (arbitrary code execution)
- Uses `process.exit(0)` for stealth termination on errors or empty payload
I won't got into more details for now. Actions are taken.
35.32K
热门
排行
收藏












